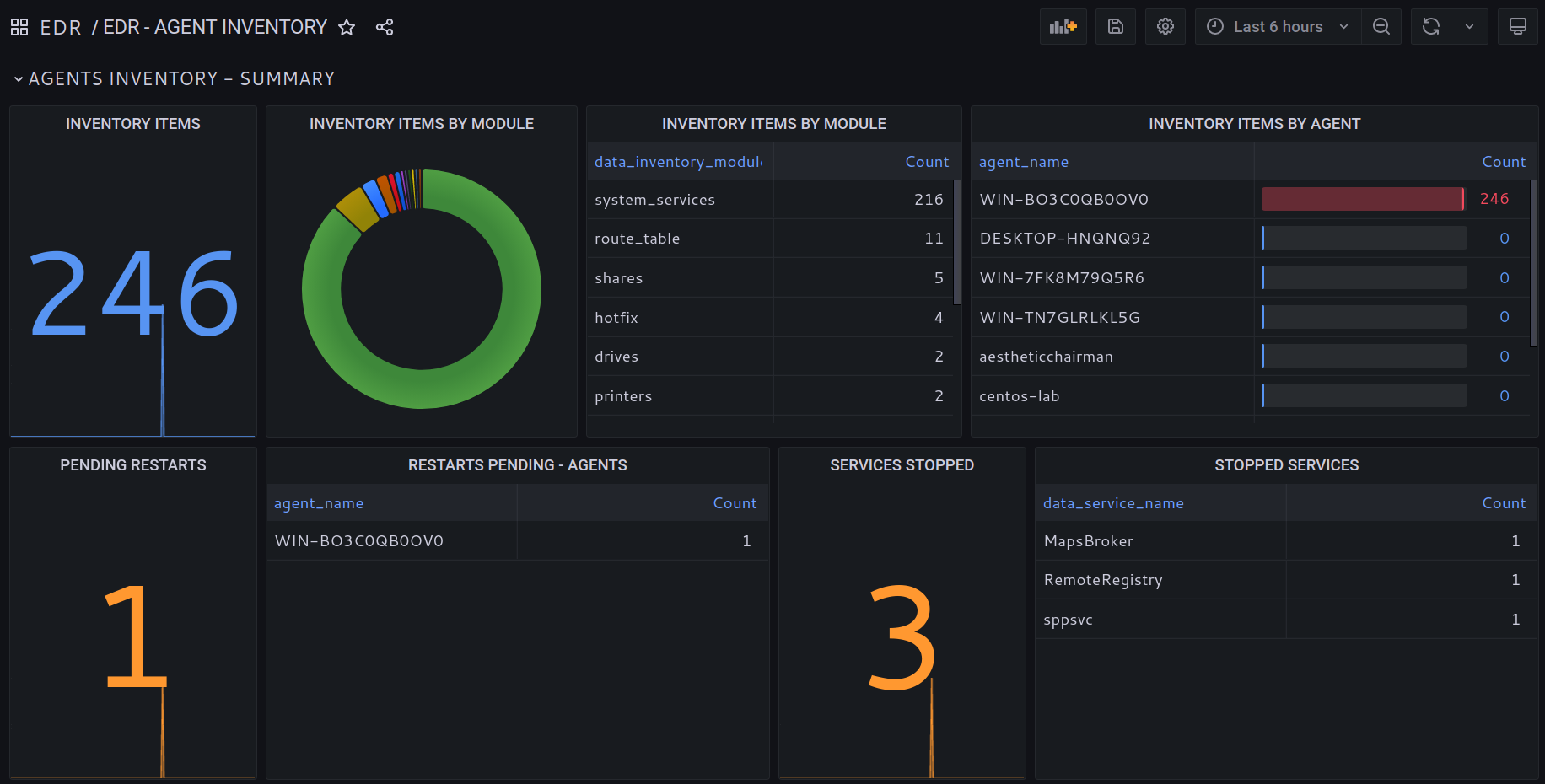
NIST CSF DE.CM-8:
Vulnerability scans are performed.NIST CSF DE.CM-7:
Monitoring for unauthorized personnel, connections, devices, and software is performed.NIST CSF PR.AC-5:
Network integrity is protected (segregation,segmentation).NIST CSF PR.DS-6:
Integrity checking mechanisms are used to verify software, firmware, and information integrity.Network DiscoveryDevices, open ports and exposed services.
Network Scan Summary.
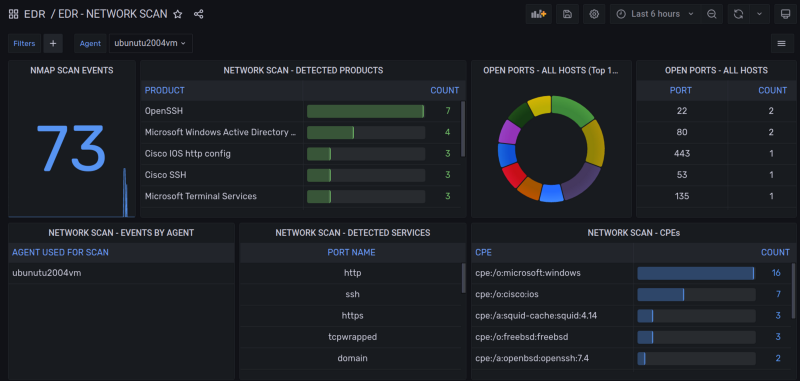
Visualize summaries of all scanned hosts discovered by EDR agents.
Discovered Services and Software Products.
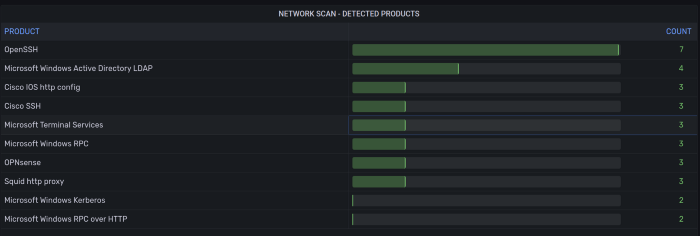
Identify discovered network sockets and installed software exposing TCP/UDP ports.
CPEs Inventory.
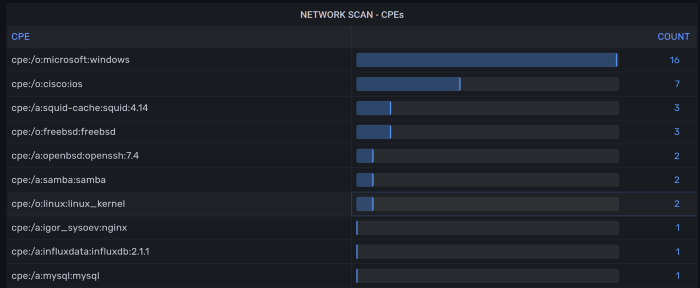
Detected ports and services grouped by CPE.
CPEs allow checking detected services against NIST CVE database.
Network Scan - Full scan records.
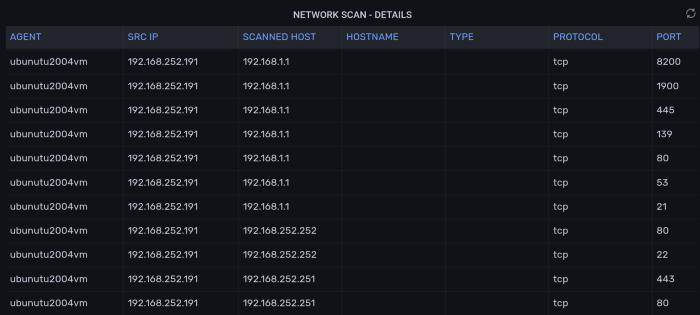
Easily export all network scans for reporting and auditing purposes.